I received a really authentic looking email message today telling me that my PayPal account had been suspended. 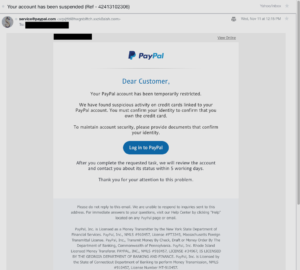
Only problem was that he email address the message was sent to doesn’t actually have a PayPal account associated with it. But given the effort that must have been taken to undertake this campaign I thought I’d investigate. Fair warning: I have worked in cyber security for years and analyzed hundreds of emails. I examine information from the email messages and strongly suggest you never follow any URL to the host site.
The first step was to look at the sender’s email address (xqxjtfd at hwgnbiftch dot xxzk8aish dot com). This turned out to be of no real value. It was not from the PayPal domain and running the domain it was from through VirusTotal yielded little information other than the domain ‘xxzkaish dot com’ was likely dynamically generated. None of the VirusTotal engines saw this as malicious.
The next step was to look at the link in the email message itself. Putting myself in the threat actors shoes for a moment what they were trying to do is to elicit an ‘aw shit’ emotion and get the reader to click on the PayPal login link in the message. That ‘Login to PayPal’ link in the message was interesting in that it resolved to LinkedIn dot com. 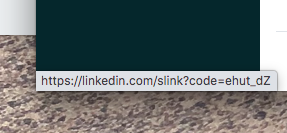
LinkedIn does offer a URL shortening capability. In fact if you share a link that is longer than 26 characters in a LinkedIn post they automatically shorten the URL. Note: I have contacted LinkedIn Support asking if this is a genuine LinkedIn shortened URL and if they can share with me the post or profile that the URL was generated from. From the safety of a virtual sandbox I followed this LinkedIn URL.
As you can see the LinkedIn shortened URL produces a recent screen copy of the PayPal login screen. The big red flag is the URL for that login page being from the’kozow dot com’ domain. As of this writing running the complete domain ‘aotsuruz0e dot kozow dot com’ through VirusTotal resulted in three engines identifying this as either phishing (Emsisoft and Google Safebrowsing) or malicious (Netcraft). Running just the top level domain ‘kozow dot com’ through VirusTotal resulted in just two engines (Emsisoft and Netcraft) producing results.
Going further and looking at the words used I called up Google Translate. I believe that the sender email address was likely dynamically generated and resulted in no translation. The domain used to display the PayPal login used two words. The word ‘aotsuruz0e’ did not translate (parsing the word differently did return ‘blue crane zoe’ in Japanese) and “kozow’ in Polish translates to ‘goat’ in English.
I believe that the domain ‘kozow dot com’ has likely been hacked and is in the hands of one or more threat actors. My recommendation is that domain be blacklisted by Internet Firewalls.